
The Browser
for Business
Secure your workforce without
compromising speed and usability.
Zero Trust Browsing
- Developed from the ground up with cybersecurity, encryption, and data management tools


Paradigm shift
Data Security
Fully control access to corporate applications, databases or specific functions with fine grained role-based access controls + risk based MFA.Read More About this TopicData Control
Set granular policies that keep data where it is supposed to be and effectively prevent data leakage - irrespective of device or location.Read More About this TopicData Visibility
Centralize visibility into your entire organization and allow employees the secure freedom of remote or hybrid work.Read More About this Topic
Work Safer, Faster and Easier
With Primary, security and productivity are built into the foundation of your operations—streamlined, secure, and effective
Read More About this Topic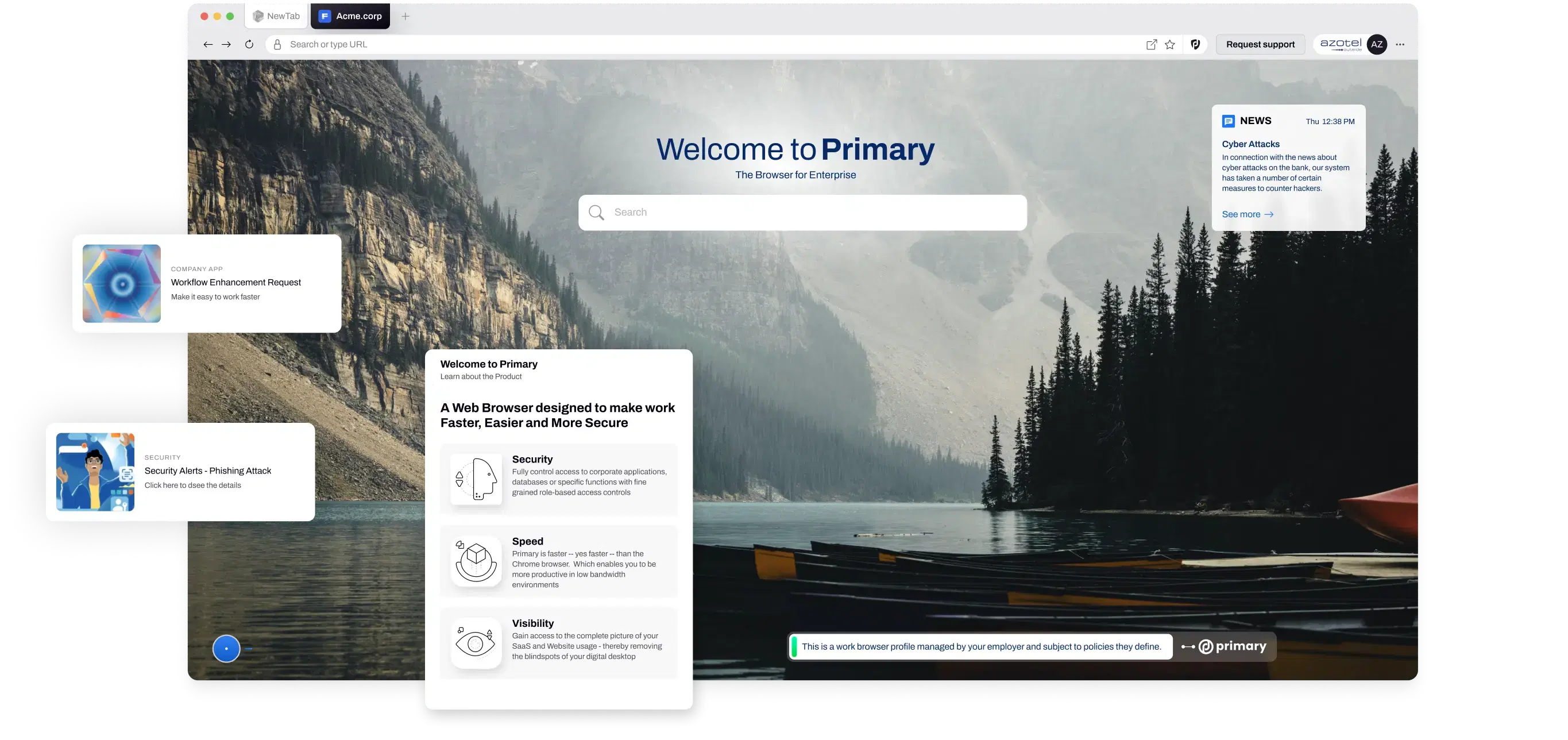
Latest news
Explore expert insights, practical tips, and best practices for safeguarding sensitive data and building enterprise resilience. This resource offers deep dives into cybersecurity trends, emerging threats, and technologies designed to help your business thrive in a rapidly evolving digital landscape.
See all blog posts

Must readApr 08, 2025
When Your Browser Becomes the Weak Link: The Hidden Risks of Extensions
Read More About this Topic
Must readFeb 21, 2025
Misconfigured SaaS Apps: The Silent Data Breach Threat (and How to Stop It)
Read More About this Topic
Redefine Secure Browsing
Gain control & protect your organization’s sensitive data with a browser built for the modern enterprise. Discover how the right browser can transform your security strategy.



